Cybersecurity: prevent the theft of your data
An employee in your business inadvertently clicked on a link from an unknown email? A cyberattack has allowed an individual to steal the sensitive data contained in your computer system?
Regardless of where they happen, these situations occur more frequently in local businesses than you would think. Not only is hacking costly for your organization, but it could also shake your customers’ confidence. To prevent this from happening, you must implement measures to strengthen your business’s cybersecurity.
01
Know how to recognize fraudulent emails
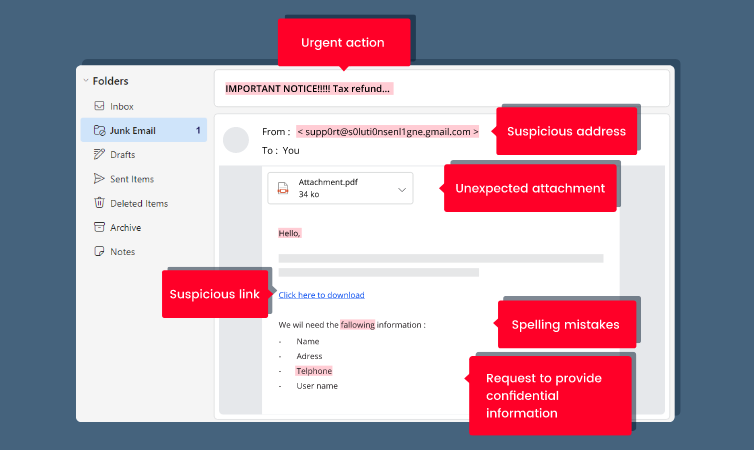
A lot of hacking is caused by malicious links in emails which seem trustworthy (“phishing”). However, several distinct signs can help you check if an email is safe.
For example, it is recommended that you look at the sender’s email address to ensure that it is trustworthy. Some fraudsters modify or add letters to the address so that it looks like a real email address at first glance.
When you read the message in the email, pay special attention to spelling mistakes as well. Unlike the emails sent by businesses, fraudulent emails regularly contain mistakes and even include links with spelling mistakes. If you see a pixelated and deformed logo in your email, it probably means that it has been trafficked from an email from a trustworthy source.
Most fraudulent emails also contain messages and a link urging you to take immediate action, such as updating your banking information or collecting a refund from a tax agency. Keep in mind, however, that a reputable business or person would never send you this type of message, especially when you are given a very short time to respond. In other words, always be vigilant and make the necessary checks before clicking on anything.
02
Use cybersecurity applications
To ensure their network’s cybersecurity, many organizations use specially designed devices to protect confidential information. For example, antivirus software is very useful for detecting security breaches on any computer.
Don’t forget to regularly update your antivirus! By doing so, it can continue to handle additional security breaches which could otherwise harm your business. It is also very important to protect your documents and computer workstations by using several different passwords, which you should changer regularly.
03
Encrypt and separate your data
If you regularly transfer sensitive information to trustworthy people, it is strongly recommended that you acquire a solution capable of encrypting your data, i.e. making them inaccessible and unreadable unless you obtain a specially designed key to decrypt them. Therefore, even if your computer workstation is hit by a cyberattack, the fraudster cannot access your confidential data.
To avoid the complete loss of your data, you can also create several copies of your backup and put them in several different places. Therefore, if a computer virus forces you to format your computer or network, you will not lose any essential information.
04
Use a cloud solution
Rather than transfer your data by email, you can also send them to trustworthy people using a cloud solution. With this type of application, you always have access to your information in a secure environment.
You can use this very affordable service to automatically save all your documents in the same place and even consult them from your telephone. For example, if you choose to send your financial statements to your accountant, they simply have to login to the corresponding application to view them at any time.
Did you know that the Acomba GO software also offers such a solution to all its customers? Whether you manage a small or a large business, you will never need to worry about the security of your confidential information thanks to an easy to use application designed to meet the needs of local entrepreneurs. Do not hesitate to talk to our experts for more information about our customized management tools!

The Acomba blog is brimming with articles on business, IT and business management.
Subscribe so you don’t miss a thing!

I am already subscribed